- Welcome Guest
- Sign In
- Welcome Guest
- Sign In
Tech industry analyst Mark Vena explores how Qualcomm, AMD, and Intel are pivotal in driving AI-enabled advancements in PCs, potentially triggering a supercycle in sales amidst fluctuating market conditions an...

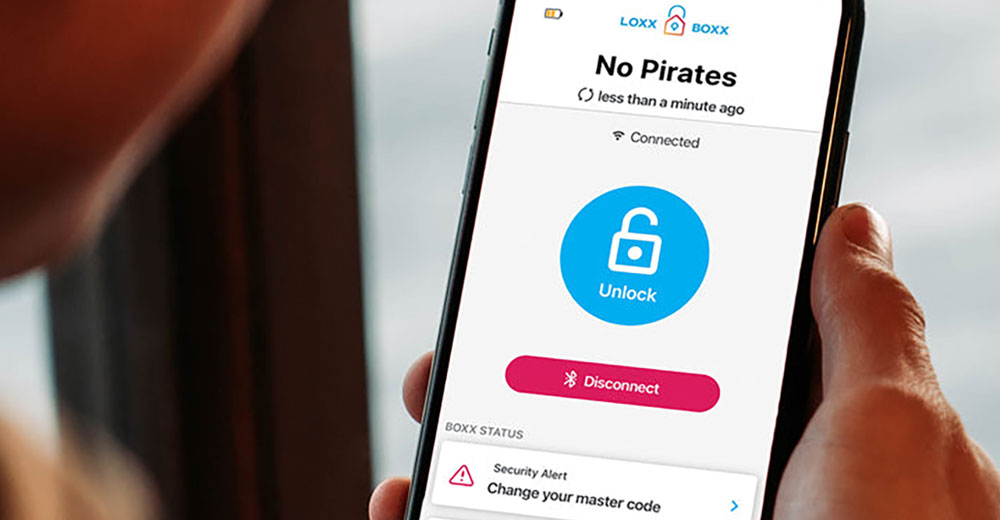
Brute force cracking of passwords takes longer now than in the past, but the good news is not a cause for celebration, according to the latest annual audit of passwor...

ConvertKit founder and CEO Nathan Barry bootstrapped his startup strategy 11 years ago with only $5,000 and a small garage to grow his fledgling firm into a $30 million business...

Nearly two dozen dating apps were flagged by Mozilla's Privacy Not Included researchers as failing to meet privacy and security standards, sharing customer data with third parties, and excluding th...

Qualcomm has unveiled a new AI-ready IoT platform for home and industrial use and introduced service-defined Wi-Fi, both of which aim to improve the functionality and reliability of smart home...